How to Backup and Restore a Bitcoin Wallet

A wallet backup is an essential measure to protect your bitcoins in case of computer or software failure, as well as to provide a way to recover your funds if your device is stolen or lost. The backup contains the necessary information, such as private keys or seed phrases, that allow you to regain access to your funds.
Computer or software failures can occur due to hardware malfunctions, operating system crashes, or data corruption. If you don't have a backup of your wallet, you risk losing access to your bitcoins and may find it difficult, if not impossible, to recover them.
To ensure the effectiveness of your wallet backup, it is important to follow proper security practices. Here are a few key points to consider.
Offline storage
Offline storage is indeed a highly secure method for storing wallet backups. By keeping your backups offline, you significantly reduce the risk of unauthorized access by hackers or malware. Here are some key advantages of offline storage:
- Increased Security: Storing wallet backups on external hard drives, USB drives, or paper wallets provides an additional layer of security. These physical storage options are not connected to the internet, limiting the exposure to potential online threats.
- Protection Against Online Attacks: Hackers and malware often target online storage solutions. By storing backups offline, you eliminate the risk of cyber attacks aimed at compromising your wallet backups. This is particularly crucial for long-term storage of significant amounts of cryptocurrency.
- Safeguarding from Hardware Failure: Storing backups on external devices can protect your wallet data in case of hardware failures. If your computer or online storage experiences a malfunction, having offline backups ensures you can recover your funds without relying solely on one source.
- Physical Control: Using physical storage methods, such as paper wallets or devices like Cryptosteel Capsule, allows you to have full control over your wallet backups. You can store them in a secure location, such as a safe or a bank vault, reducing the risk of loss due to theft or physical damage.
However, it's important to consider some potential drawbacks of offline storage:
- Physical Vulnerabilities: While offline storage protects against online threats, it introduces physical vulnerabilities. External devices can be lost, stolen, or damaged. Proper security measures, like encryption and off-site backup, should be considered to address these risks.
- Accessibility and Convenience: Offline storage can be less convenient and accessible compared to online solutions. If you need to access your funds frequently, it may require additional steps to retrieve and restore your wallet backups. Finding the right balance between security and convenience is important.
In summary, storing wallet backups offline provides a highly secure method for protecting your cryptocurrency assets. By disconnecting the backups from the internet, you minimize the risk of unauthorized access by hackers or malware. However, it's crucial to handle the physical storage media with care and consider contingencies for potential loss or damage.
There are generally three ways to back up a Bitcoin wallet, each supported by different software.
Please ensure that you are familiar with your wallet before loading it with bitcoins. If you lose the backup and cannot access your wallet for any reason, your bitcoins will be permanently lost!
#1 BIP 39
BIP 39 provides a practical and standardized method for generating mnemonic sentences that represent seeds for wallet addresses. By enabling users to easily remember and record these mnemonics, BIP 39 enhances the accessibility and usability of cryptocurrency wallets, while still maintaining a high level of security.
When you create a wallet for the first time, instead of dealing with complex cryptographic keys directly, you are provided with a mnemonic sentence. This sentence comprises a list of 12 to 24 words chosen from a predefined set. The words are carefully selected to ensure they are distinct and unambiguous, making it easier for users to remember and record their mnemonic.
The number of words chosen for the mnemonic has a direct impact on the security level of the wallet. With a larger word count, the entropy and cryptographic strength of the generated seed increase. Consequently, it becomes more challenging for an attacker to guess or brute-force the seed and gain unauthorized access to the wallet.
Some wallets, such as Trezor, offer users the option to select their own entropy. This means that rather than relying on the wallet to generate a seemingly random mnemonic, users can provide their own personal set of words to create the seed. By choosing their own entropy, users have the advantage of incorporating memorable information into their mnemonic while maintaining the overall security of the wallet.
Backup
To securely protect your words, you can follow a couple of approaches. The first method is to write down the words on a piece of paper and store it in a secure location like a vault. This ensures physical security and safeguards your information from unwanted access.
Alternatively, you can apply a technique known as Shamir Secret Sharing to divide your secret into multiple parts. The Shamir secret sharing algorithm is specifically designed to split a secret, like your seed phrase or cryptographic keys, into several shares or fragments. These shares are created in a way that only a specific number of them are required to reconstruct the original secret.
By employing Shamir Secret Sharing, you can distribute the different shares of your seed phrase across various locations. For instance, you can divide the secret into three shares and hide each share in separate secure spots. This way, even if someone discovers one of the shares, they won't be able to reconstruct the original secret without obtaining the other required shares.
Cryptosteel Capsule
When it comes to securely storing each Shamir share, one highly reliable option is the Cryptosteel Capsule. The Cryptosteel Capsule is a robust and tamper-proof device designed specifically for the purpose of safeguarding sensitive information, such as cryptographic keys or in this case, Shamir shares.
This compact storage device is built to endure extreme conditions, including fire, floods, and corrosion. Its construction consists of high-quality stainless steel, which provides exceptional durability and resilience. This ensures that the Shamir shares stored within the Cryptosteel Capsule remain safe even in the face of physical threats.
One of the notable advantages of the Cryptosteel Capsule is its simplicity. The device does not rely on any electronic components or power sources, making it impervious to hacking attempts or technological failures. This feature eliminates any concerns about electronic vulnerabilities, ensuring that the Shamir shares are stored securely and shielded from digital threats.
Additionally, the Cryptosteel Capsule offers a strong defense against tampering or unauthorized access. Its solid construction makes it nearly impossible to tamper with or break open without leaving visible signs of compromise. This makes it an excellent choice for storing sensitive information, such as the essential Shamir shares, where maintaining the integrity of the data is of utmost importance.

Restore
To restore the backup, open your wallet software and locate the New/Restore feature in the menu. When prompted, type in the mnemonic from your paper in the exact order.
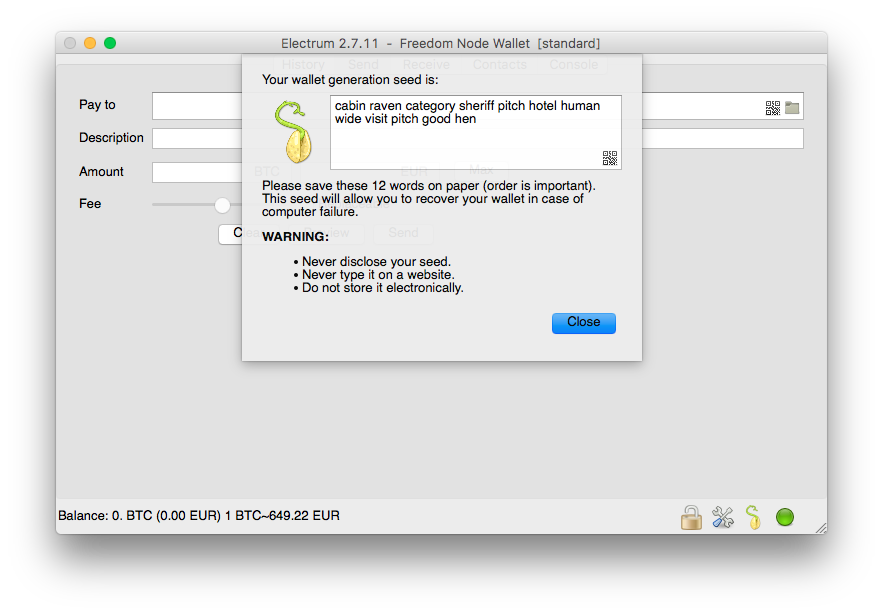
Once you have entered the mnemonic, the wallet software will determine the remaining keys and addresses associated with your wallet. Additionally, the software will restore your transaction history from the blockchain, ensuring that all your previous transactions are reflected correctly.
However, it's important to note that the restoration process does not include certain metadata, such as contacts or transaction labels. If you require this information, you will need to backup a wallet data file as well. The process of backing up this file may vary, as it depends on the specific wallet software you are using. The location and filename for the wallet data file will be different for each wallet, so it is not possible to provide specific instructions in this post.
#2 BIP 32
BIP 32 provides a standardized method for deriving key pairs from a single seed. This seed acts as the foundation for generating a master private key (xprv). Once you have obtained the xprv, you can import it into any HD (hierarchical deterministic) wallet that adheres to the BIP 32 standard.
xprv9s21ZrQH143K2PXgtDvNp1e5Mzxncb3D3qM7pcXEp6eaSZ8HNaUxb18ohbw9jqRkGaYhquPmn1rH2BxnQ54uEMrw8xxaUSo3KxnrCJ3AaD7Backup
When it comes to backing up your wallet, there are a couple of recommended approaches.
The first option is to securely copy the master key and save it in a text file. It is essential to encrypt this file and store it on a separate device, adding an extra layer of protection to your funds.
Alternately, you can choose to create a QR code representing the master key. Printing out this QR code and storing it in a secure location, such as a vault, ensures that you have a physical copy of your key.
It is crucial to note that if you opt for storing the master key as a QR code, you should disconnect your device from the internet during the process. This precautionary measure prevents any potential unauthorized access to your key, ensuring the safety of your funds.
Restore
To restore a backup, you simply need to paste the xprv string into your wallet when prompted. Luckily, most BIP 32 compliant wallets support this feature. However, if you come across a wallet that does not support restoring from an xprv string, it is advisable to steer clear of using it. Opting for wallets that adhere to the BIP 32 standard ensures a seamless and secure backup and restoration process for your funds.
#3 Wallet.dat
The method mentioned is considered outdated and is primarily employed by older Bitcoin Core wallets. It involves the process of backing up a file named wallet.dat. This file serves as a repository for various essential components, including keys to spend outputs, addresses, transaction details, and additional metadata like contacts.
The specific location of this file will differ based on the operating system being used.
Windows: %APPDATA%\Bitcoin
Linux: ~/.bitcoin/
Mac OS X: ~/Library/Application Support/Bitcoin/
If you are unable to locate the precise location of the wallet.dat file on your system, please refer to this page.
Backup
Firstly, locate the wallet.dat file and copy it to another device that is only accessible by you. There are several options for storing the backup file securely.
One option is to use a USB drive or CD, as these physical devices can be easily stored in a secure location. They are not connected to the internet, reducing the risk of unauthorized access.
However, it's important to remember to update the backup regularly, especially if there are any changes to your wallet.
Another option is to copy the wallet.dat file to another computer that you have exclusive access to. This can be a safe approach, as long as the second computer is properly secured and protected from potential data breaches.
If you decide to use a cloud storage service, such as Proton Drive, it is crucial to encrypt the wallet.dat file before uploading it. Encryption ensures that if someone gains unauthorized access to your cloud storage, they won't be able to read or use the file without the decryption key and steal your bitcoin.
Restore
To restore the backup, all you need to do is copy your backed-up wallet.dat file and then replace the existing one in the bitcoin data location.
Secure location
Storing backups in a secure location is crucial for ensuring the safety and integrity of your data. Here are some further points to consider:
- Safe or Lockbox: Investing in a fireproof and waterproof safe or lockbox can provide a high level of protection for your backups. Look for one that is specifically designed to withstand extreme conditions. This ensures that, even in the event of a fire or flood, your backups remain unaffected.
- Hidden Spot in Your Home: If a safe or lockbox is not an option, you can still choose a hidden spot in your home as long as it meets certain criteria. The location should be discreet and not easily accessible to potential thieves. Consider places like a hidden compartment, a locked cabinet, or a container within a larger item that doesn't immediately attract attention.
- Protection from Fire: Fires can cause irreversible damage to your backups, so it's essential to protect them against this threat. Opt for fire-resistant storage options that provide a high degree of insulation from heat, flames, and smoke. Additionally, avoid storing backups near potential fire hazards or sources of heat.
- Protection from Water Damage: Water damage is another common threat that can destroy your backups. Ensure your chosen location is well-protected against water-related incidents, such as leaks, flooding, or accidental spillage. Avoid storing backups in areas prone to moisture, such as basements or near pipes.
- Protection from Theft: It's important to safeguard your backups from theft. Choose a location that is well-hidden and secure, minimizing the risk of unauthorized access. Consider utilizing additional security measures for added protection, such as alarms, surveillance systems, or even a professional security service if necessary.
- Redundancy: Consider storing multiple copies of your backups in different secure locations. This provides an extra layer of redundancy, ensuring that even if one location is compromised, your data remains intact elsewhere. Separate these locations geographically, if possible, to minimize the chances of all backups being affected by a single event or disaster.
Remember to periodically review and update your chosen storage locations to account for any changes in your home or security conditions. By implementing these measures, you can significantly reduce the risks associated with data loss, ensuring the long-term security of your backups.

How to safely backup your crypto savings
Never lose your coins to a hardware failure or thieves. Protect your bitcoin!
Encryption
Using strong encryption and security measures for cloud storage backups is essential to protect your data from unauthorized access. When selecting a cloud storage service, it is crucial to verify that they offer robust encryption and security protocols. This ensures that your data is protected both during transmission and while at rest on their servers.
One such solution that combines strong encryption and privacy is Proton Drive a part of the Proton suite of privacy-first tools.
However, to add an extra layer of protection, you can encrypt your backup files yourself before uploading them to the cloud. By doing so, you retain complete control over the encryption process and the encryption keys. This approach is commonly known as client-side encryption.
Encrypting your backup files before uploading them provides several benefits:
- Enhanced security: By encrypting your files independently, you are in control of the encryption algorithm and key management. This means that even if the cloud storage service experiences a security breach, your data remains secure.
- Protection against unauthorized access: Encrypting your backup files ensures that only individuals with the correct encryption keys can access and decrypt the data. This significantly reduces the risk of unauthorized access, protecting your sensitive information.
- Data integrity: Encryption not only prevents unauthorized access but also verifies the integrity of the data. Any unauthorized modifications or tampering attempts will render the encrypted backup files unreadable, providing an additional layer of protection.
To encrypt your backup files, you can use various encryption software or tools available in the market. It is important to choose a reliable and trusted encryption solution that suits your needs. Make sure to select an encryption algorithm widely regarded as secure and manage your encryption keys securely.
With strong encryption and client-side encryption practices, you can significantly enhance the security and confidentiality of your backups stored in the cloud.
Test your backups
Testing backups is indeed a vital step in ensuring the integrity and reliability of your backup system. By conducting regular test restorations, you can verify that your backup process is functioning correctly and that your files can be successfully restored when needed. Here are some important points to consider when testing your backups:
- Frequency of testing: It is recommended to test your backups periodically. The frequency will depend on various factors, such as the importance of the data and the criticality of the systems being backed up. Ideally, testing should be performed regularly, such as monthly or quarterly.
- Separate device or environment: To conduct a test restoration, it is essential to use a separate device or environment. This ensures that the restoration process doesn't interfere with the original system and allows you to identify any potential issues or conflicts that may arise during the restoration.
- Test different backup types: It's important to verify the successful restoration of different backup types, such as full backups, incremental backups, or differential backups. This will help you ensure that all backup types are working as intended and that data can be recovered from each backup type.
- Validate data integrity: During the restoration process, it is crucial to verify the integrity and completeness of the restored files. Check that all the necessary files are present, that they haven't been corrupted or modified, and that their permissions and attributes are intact.
- Document and analyze the test results: Keep a record of the test restorations performed and the results obtained. This documentation will serve as a reference for future comparisons, tracking any issues identified, and ensuring improvements are made to the backup process if necessary.
- Consider automation: If possible, automate the test restoration process to make it easier to incorporate into your regular backup maintenance activities. Automation can help streamline the testing process and ensure that it is not overlooked due to time constraints or human error.
By following these practices, you can confidently rely on your backup system, knowing that your data is properly protected and recoverable. Regular testing will help identify and resolve any issues in the backup process, enabling you to safeguard your valuable data effectively.
Protect backup passwords
Protecting backup passwords is crucial for maintaining the security of your wallet backups. Here are some practical tips to ensure the safety of your backup passwords:
- Use a strong and unique password: Your backup password should be complex and difficult for others to guess. It's recommended to use a combination of uppercase and lowercase letters, numbers, and special characters. Avoid using personal information or easily guessable patterns.
- Avoid reusing passwords: It's essential to use a unique password for your backup. Reusing passwords across multiple accounts or services can lead to a domino effect if one of your passwords is compromised.
- Avoid storing passwords with backup files: Keeping your password separate from the backup files adds an extra layer of security. Storing your password alongside the backup files increases the risk of unauthorized access in case the files are compromised or misplaced.
- Use strong encryption: Ensure that your wallet backups are encrypted using a reliable and strong encryption algorithm. This adds an additional layer of protection by making it more challenging for potential attackers to decrypt your backup files.
- Choose secure storage: Store your backup files and passwords in a secure location. Consider using encrypted external storage devices or cloud storage solutions that provide strong security measures, such as end-to-end encryption.
- Consider multi-factor authentication (MFA): If your wallet software or storage solution allows it, enable multi-factor authentication. This adds an extra layer of security by requiring an additional verification step, such as a code from your mobile device, when accessing your backups.
- Regularly review and update passwords: Periodically review and update your backup password to maintain its strength and security. It's a good practice to change passwords every few months or immediately if you suspect any compromise.
By following these best practices, you can significantly enhance the security of your backup passwords and safeguard your wallet backups from unauthorized access. Remember, securing your backup passwords is just as important as protecting the backups themselves.