You have nothing to hide: Replacing Telegram, Twitter & YouTube

Young people use Discord and enjoy networking in the communities there. Russians and Yankees use Telegram massively and replicate their memebionts across the world. Elon Musk is constantly producing buzz about Twitter. And so on. There are debates about some kind of "privacy" and "security" around it as well as how many people are using a particular social network.
But how do we navigate the social networking and messenger environment sensibly and without harm if we want to be truly 'private' and 'secure'?
Privacy
Privacy means intimacy. It is a word that describes our willingness to share data with some specific people. Most importantly, we all perceive privacy differently. Our individual level of willingness varies, the type of data we are and are not willing to share varies, and so do the people with whom we are/are not willing to share that data.
Fortunately, our culture, with its complexity, has also given us a lot of beautiful tools that allow us to have some control over our privacy. For example, we have clothing that we can use to cover our naked bodies. We have doors on toilets and bathrooms. Our mobile phones have lock screens. We use all sorts of passwords, we create communities, social bubbles, we talk to other people about other things depending on how "fit" our data is to them. And so on.
Network effect and laziness
Different people have different approaches to privacy. For example, when I talked to my friend Peter "Sue" Sagat about encrypted communication, he told me that he is a big fan of encrypted communication, but he personally doesn't address it much – everything that comes out of Peter in some form in the physical and digital world is automatically "revealed" to Peter. And the "unrevealed" Peter will take with him to his grave. The "unrevealed", according to Peter, is a kind of core of his consciousness that no one but him knows about (or perhaps someone would only know about it if they managed to scan and interpret Peter's brain with some amazing sci-fi device).
Ordinary people who don't really "address" encrypted communication are usually not as sophisticated as Peter. They may wear clothes and lock themselves in toilets, but once you discuss with them whether they are comfortable sending sensitive data through potentially dangerous messengers or other tools, you usually get a "I have nothing to hide" response (as opposed to toilet needs and naked bodies).
And yes, as you may have already noticed, the "I have nothing to hide on messenger" analogy is very similar to the "I have nothing to hide on the toilet" analogy. But importantly, even those who don't use encrypted messengers because they supposedly "have nothing to hide" don't have such a stupid analogy in their lives.
After all, who among them posts all of their every current survival publicly to their Facebook feed? How many of them create Facebook Messenger groups with their own parents and with their high school friends? How many of them put on their Instagram bio that they are currently in Bratislava, that they are gay, or that they are carrying five grams of marijuana?
Of course, most of the above doesn't happen among people who "have nothing to hide." They, too, have a natural need to hide something – to filter and direct the flow of their thoughts and actions according to how much they are willing to share them with their receivers.
And why aren't these people interested in encrypted messengers despite the fact that they are somehow interested in privacy in the digital world? Well, it may simply be that these people are lazy to switch to a more secure alternative. Or maybe it's the network effect.
And what is the network effect? In economics, the network effect is a phenomenon in which the value or utility that a user gets from a good or service depends on the number of users of compatible products.
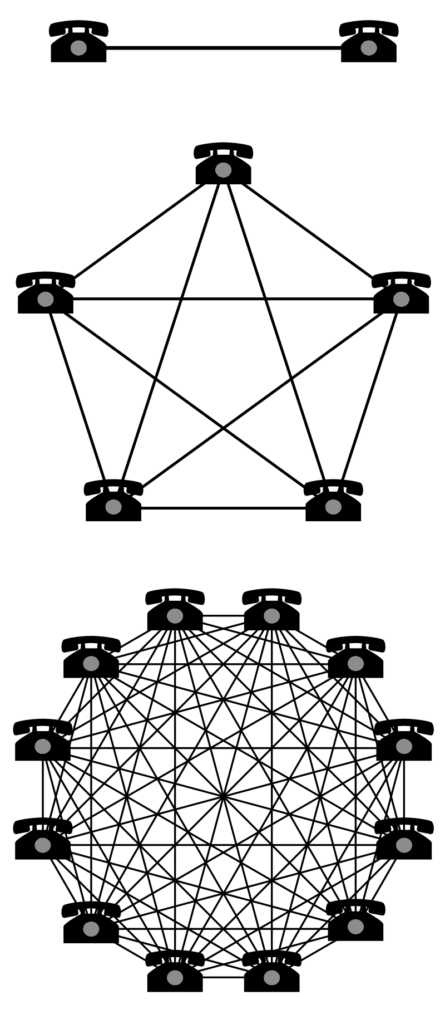
And what does this mean in practice?
Well, for example, I myself claim to be a fan of encrypted messages, but I am a boomer who uses Facebook, or an influencer who takes a picture of his swollen face in the mirror in the morning for an Instagram story. And the key reason I do this is the aforementioned network effect – my benefit from using a given tool is determined by how big and how dense the network of people using that tool is. On Element, with my server resource, I can't find (almost) absolutely every single person in the world from any social class, country, or age group. With Instagram, for example, I can do it with much less effort.
So logically, if I like a tool and want more people to know – and more importantly use it – I need to increase its network effect. Nagging is a beautiful tool for increasing network effect. I do it wherever I can. Many times I am rude and expressive, and just as I fanatically impose other technologies on people, I also impose alternatives for encrypted messengers and social networks.
After all, even this article will be a mere nag. A nagging in which I want to get a little more into the world of the most useful thing I see in my social bubbles. Whether it's shit like Instagram or Facebook, or messengers, which a lot of people think are really encrypted and therefore use to share really sensitive data.
In this article, we're going to cover messengers and social networks in particular. There are many other privacy and security tools in the digital world, but maybe we'll talk about them later.
The storm of messengers
Violations of privacy lurk everywhere and are not only the privilege of hackers, but also the privilege of governments. Big Brother is reaching into software that we often think is in our hands and doing something we don't (and probably won't) know about. And this is far from being a specificity of the world of totalitarian politics. Even India, 'the world's largest democracy', invented 11 years ago a state-run spying system called NATGRID, which collects internet logs, login details, driving licences, salaries and other crap from virtually everyone in India and builds up a KYC database from it.
Europe, unlike India, is somewhat better off (or so it tells its citizens; and even if it censors and monitors different things than India). However, we don't really know the reality.
What we do know about the US government, thanks to Edward Snowden, is that it spied on its own citizens in 2013 using the XKeyscore system. How the US government has (and has been) messing around with codes and global surveillance since then, we also don't know very much anymore.
All of the governments mentioned above guard their privacy carefully. However, they are aggressive entities because they are not shy about violating the privacy of other entities.
Well, if we want to avoid the mysterious background of big brother applications (and avoid the possible violent behaviour of governments or other aggressive entities), we should in principle use technologies that are in some way open and transparent.
That is, we should discourage people from communicating via Messenger or primitive instagram "paper planes".
(My Indian friend Sahid, told me an interesting story about what happened to him last year in the state of Gujarat. Gujarat, Gandhi's birthplace, is the so-called "dry state" and the consumption of any kind of alcohol is prohibited by law. Well, our dear Sahid was so confident in Gujarat that he arranged an alcohol meeting with a friend over WhatsApp messenger (among other things, WhatsApp claims to be end-to-end encrypted). And while Sahid did arrange an alcohol meet, he was raided by the police at his home the next morning. And it couldn't have been anything other than the police getting hold of Sahid's WhatsApps message).
And Sahid's story brings me to a very important point in our article. Just because an app claims to be encrypted doesn't necessarily mean it's secure, or that it really is encrypted. And as many of us already know, just because something is open-source doesn't necessarily mean it's free of security vulnerabilities either. In life (and not just with encrypted communications), to understand all the possible and impossible risks of using a tool, we first need to understand how that tool works and what it actually does.
Telegram
Telegram is something I mentioned in the introduction of the article. It's a supposed open-source encrypted rescue in the world of mysterious Big Brothers. Little kids who want to study social sciences have it, and all sorts of (and not just Russian) IT people have it. Even Dave Asprey, the biohacking guru himself, recommends it in his instagram stories. Because of the network effect, I also have it on one of my mobile devices (although I have it in a sandbox and don't use it at all).
Admittedly, I'm not a big fan of Telegram. Personally, I don't find it much more secure than Facebook messenger with encrypted communication turned on. All Telegram messages, including their history, can be cheerfully read in plaintext on the servers by anyone who has access to them, anyone who can successfully authenticate themselves there using your phone number, or anyone who can convince Telegram operators to give them the data – for example, by court order, or by threatening to arrest (or why not even martyr) family members. And since Telegram's founder is Russian, I don't think we need to doubt that something like this could happen.
Well, and all this mess applies to whoever you communicate with, your communications with each other are stored on both accounts (well, and with a Telegram group, this problem multiplies with the number of members).
Anyone interested in the larger technical details of Telegram shouldn't miss the fact that Telegram doesn't use HTTPS/TLS, but has its own encryption scheme routed to the Telegram server. More information can be found at this link.
Of course, perception of risk, perception of threat and most importantly perception of privacy is individual. I don't use Telegram because I don't like to use bad technology for the network effect. I prefer to build network effect to good technologies.

Signal
For me, Signal is the tool that fulfills a similar function in my life as Telegram does for other people.
With Telegram, we mentioned the not very happy architecture around the servers as a major drawback.
All your Signal conversations are stored only on your device by default. In Telegram, they're stored on Telegram's servers and can be synchronized between your devices. That basically means that Signal servers can forward messages, but they cannot see their content.
Unfortunately, the big disadvantage of Signal over Telegram's services is the user experience in groups. Yes, in those groups that are so "multiply" vulnerable on Telegram in terms of not-so-happily obfuscated access to data on the servers. Among most people I know, Telegram is so popular precisely because of its support for bots, whose integration is unfortunately not supported by Signal. However, there is another messenger, Element, for the bot function from my point of view, which we'll talk a bit about in the chapter below.
We know that groups in Telegram are not end-to-end encrypted, and thus the encrypted communication is between your device and the Telegram server, which sees the content of the communication in the groups. On the other hand, it is a characteristic of Signal servers that they can't even see the membership of groups (especially not their name or content).
Telegram is also censored, especially the Android version from the Play Store. Fortunately, with Signal, we can verify that the Play Store app is compiled from source without adding any additional code.
Signal is, from my point of view, a pretty nice and well made app. You can, of course, delete messages in it a few minutes after sending them, but a particularly interesting feature of Signal, which is missing in, for example, messenger Threema (and for which Kočner's Threema became famous), is the ability to configure "disappearing messages". This can be set both in private conversation and in a group, and the setting can be changed at any time. Disappearing messages ensure that everyone who sees a given message deletes it from the device after a certain amount of time (1 hour, 8 hours, a day, a week…).
Signal beta also allows the same stories as, for instance, the social network BeReal, but of course the Signal ones are encrypted.
But not to just praise Signal, we have to mention that one of its main drawbacks in terms of privacy is its being tied to a phone number (although this can be solved via an anonymous SIM card). On the other hand, it helps Signal's network effect a lot – if you want to write to someone and you have them saved in your phonebook, they're automatically saved on Signal as well. And just like the problem of missing bot integration, the problem of being tied to a phone number is also solved by another encrypted messenger Element.
Discord? No, I prefer Element!
A lot of people use Discord primarily because of three things. Because of the communities, because of the bots, or because of the network effect. The last thing I accept, but the first two I don't. For communities and bots, I recommend using Element. Discord is a pretty unfair platform from my point of view (among other things, 11 year olds make money on Discord spreading malware) and in my life I have found no other use for it than as an interpreter for the AI bot Midjourney :)
Element is a pretty interesting thingy. It's an encrypted messenger that uses the Matrix protocol. If you're comfortable with a different client application than Element, you can choose it and communicate however you like.
However, the multidimensionality of Matrix/Element goes much further than just the ability to choose a client application. You also choose the server you have your account on, which holds encrypted messages for you while you connect, and you can communicate with other users (as well) on other servers, so you're not dependent on a single operator. In addition, the whole system can also work in "island mode" – if you no longer have an internet connection but have a local server, you can continue to communicate. For example, this is currently used quite a lot in Ukraine, where local operators in individual cities run Matrix servers – if everything works, they can communicate not only between cities, but also with the whole Internet without anyone noticing that these are different servers. Even in "groups" there can be members from different servers.
You can create "spaces" in Element, which is something similar to Discord's "servers" or Slack's "teams". In addition, Element (compared to Signal) also supports voting, message editing, or you can also decide whether users who join a space will also have access to the space history or will only see messages from the time they joined the space.
Element is also without a phone number and you can register anonymously (almost nobody adds emails there). You only need to find the identifier of the person you want to communicate with.
If you want to play with your Matrix installation, you can then use Element (as a Matrix client) for virtually all your communication needs, no matter what channel your users write to you through. And that's exactly what our lovely bots are for, which Element is a great master at integrating thanks to Matrix.
The downside of Element is supposedly intermittent-instability, but I don't use it often enough to notice anything noticeable. But it's a fairly logical tax with a very decentralized server architecture.
The big downside of Element from a privacy perspective is that the servers can see who is communicating with whom (but not about what) and who is a member of what group. And that's also a tax on the decentralized architecture :)
Fediverse: Mastodon as a better Twitter?
You won't have missed how many Twitter users have taken shelter at Mastodon; an open-source, decentralised social network that is very similar to Twitter. Except that not only is it owned by Elon Musk, but no one else either.
And why am I following up on Mastodon right after the Element/Matrix talk? Well, both Element and Mastodon share a common basis, which is the so-called Fediverse. And in order to understand what the Fediverse is, we need to understand the very idea behind the creation of things like Element or Mastodon.
Facebook, YouTube and Twitter may run on different servers around the world, but they are owned by the same company. They are also closed, not only in the sense of the source code, but also in the sense that they don't communicate with each other. If you want to reach someone on Facebook, you have to create an account there.
With the opposite intention, the idea of the "fediverse" or "federated universe" was born. This is based on the principle that everyone will be able to run their own server and be able to connect with anyone. But for this to work, they have to speak the same language. In the computer world, this language is the communication protocols that define what is transmitted over the network and in what form.
In the fediverse, there are several such protocols. You have heard of Matrix, for example. At the time of writing, there is also quite a lot of talk about the ActivityPub protocol, which is backed by the W3C, arguably the foremost web authority.
ActivityPub is then also supported by individual programs (server software) and one of them is Mastodon. But ActivityPub is also used by other server software. If Mastodon is a variation of Twitter, then Friendica resembles Facebook, Peertube is inspired by YouTube, and Pixelfed has Instagram as its model again (but we'll talk more about the clients for these classic social networks in the chapter below).
Once you open Mastodon, the application asks you to register on one of several thousand linked servers (instances). You can also choose one of the default categories, where you can find, for example, a server of the Czech arch-linux community, or even a server of Korean furries.
Each user is identified on Mastodon as @name@instance. For example, on the Czech archlinux server I go by @[email protected].
If this reminds you of an email, it's no coincidence. Email is the most beautiful example of an open and decentralized service based on the fediverse principle. If you set up an account with an @gmail.com address, you can also correspond with those who have @seznam.cz, or @protonmail.com. Or you can set up your own @michalkodnar.xyz domain.
To make analogies with email and Element not too few, as with email and Element, Mastodon is just one of the client applications of that protocol.
In addition, each instance of Mastodon has its own rules.
Thus, you can create an instance that follows the laws but is not ashamed of untagged pornography (like the Koreans did). Operators of other instances may not like this and may blacklist you.
Even a foreign instance you use may one day drop out of the blue, and if you don't back it up beforehand (which you can) you will lose everything. The main disadvantage of Mastodon is undoubtedly that individual servers are quite expensive to run and not very easy to manage.
Only time will tell how it will turn out with Mastodon.
By the way, Mastodon doesn't tweet and retweet, it toots and boosts ;)
Big Brother Clients
YouTube algorithms are interesting. They collect something, they output something to us, and somewhere in between they learn what we watch. And we're not even talking about tracking, data trading, and ads in the extreme and obvious cases that Instagram, for example, does.
There's a mass battle going on in the background of our screens with apps like YouTube, Facebook and Instagram for our purchasing power and our attention. The role of big brother apps is nothing more than to keep us glued to our screens by virtue of triggering an addiction to dopamine (which is usually released after buying shoes from Wish hyperlinked by Facebook, or for a heart on one of the three hundred selfies we post daily on Instagram).
Encryption, after all, doesn't hide everything we consider part of our intimacy. Another important discipline of navigating digital space is, of course, defending against tracking and monitoring, but I won't go into that now (maybe next time).
Among other things, moving away from Big Brother and moving to encrypted and secure technologies takes with it the toll of missing network effects. Fortunately, though, we don't just have to play with encrypted "replacements," we also have clients for traditional social networks that at least somewhat purify our world from the toxic noise of Bigbrother social networks.
YouTube
YouTube without ads, without Google Framework Libraries, without the YouTube API and therefore with the possibility of background playback of whatever you're watching? Yes, that's NewPipe.
So NewPipe is a sort of front-end to YouTube that replicates a number of useful YouTube Premium features for which you'd otherwise have to shell out nearly $12 for a subscription. Instead, New Pipe is completely free.
NewPipe also supports video downloads. Let's say you have a bad internet connection and can't stream videos, but downloading is fine. Just find the video you want to save and click the "Download" button to save the files. Plus, with support for both audio and video downloads, I was easily able to cancel my subscription to Spotify. I started downloading all my podcasts from NewPipe and playing them in VLC Player.
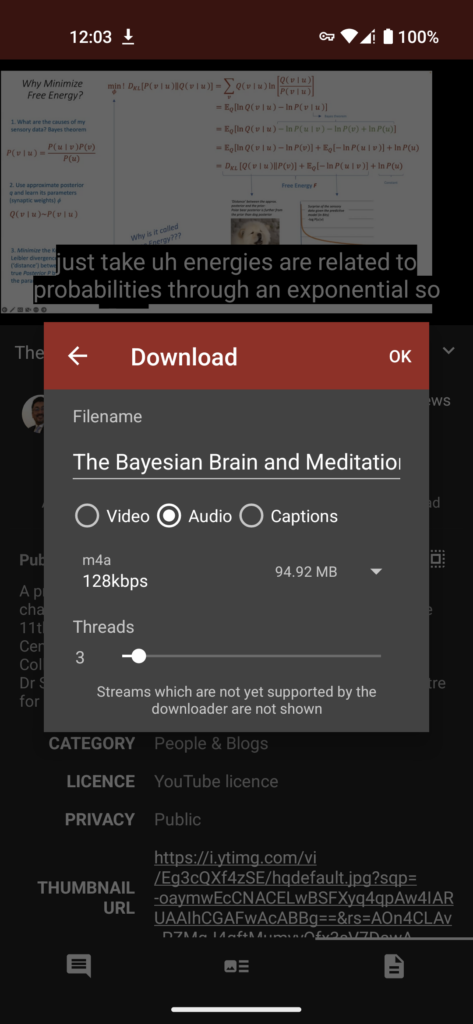
Beyond the ability to download videos and the absence of ads, NewPipe will also please true privacy enthusiasts. In fact, the app also has the ability to download videos via Tor. Streaming video files this way doesn't work yet, and unfortunately the developers forgot to mention when this feature will be added. However, it should not be forgotten that your information is stored offline on your device and NewPipe does not use any proprietary Google API.
You can learn a bit more about NewPipe at this link. It's fully opensource and you can check out its source code on GitHub.
Facebook on desktop is enhanced by a beautiful extension called Fluff Busting Purity. It allows you to remove annoying and irrelevant posts from your newsfeed, such as ads and sponsored posts. I use F.B. Purity on my desktop as well and it always lets me know, for example, when someone unfriends me from Facebook. And I know his/her name and also the time of unfriending. Or I can also filter out all posts containing the word "coronavirus" :)
Among other things, there's a lightweight, 100 kilobit open-source client for Facebook on your mobile device called SlimSocial. It's not intrusive like Facebook and it's ad-free. The app behaves differently on different hardware, but my overall impression of it is that bugs are removed rather than added. Still, given that Facebook is already just a social network for boomers, I don't really miss the "flawlessness" much either.
Unfortunately, if you want to be an influencer, there's no open-source client for you and it's a good idea to take the time and secure an instagram app from which you post your photos. If you use Android, you'll appreciate at least the Insular app, which isolates your big-brother apps, which includes Instagram.
If you didn't want to post and were content to chat ad-free completely independent of the Instagram app, you could use an open-source client called Barinsta. The app was made very nicely, but I personally didn't use it in any other way outside of testing (since practically the only meaning of Instagram for me is spamming with stories), and it's also true that nobody has seen its source code for a long time and therefore no safe updating is possible.
Personally, I'm not a big Twitterer. I follow about twenty people there and I open the app about twice a month. However, if I want to read a tweet without logging into my account, I use the open-source Twitter client Fritter. Its GUI is very nice and in many ways reminds me just of the minimalist Barinsta.
Czech anarcho-communists from NoLog.cz built something similar again this year and called it Nitter. The interesting thing about Nitter is that if you rewrite https://twitter.com/ to http://nitter.cz in the web address of a tweet or account, the content will be displayed directly in the Nitter interface. In the future, there are also plans to add a sort of timeline to Nitter, to which users will be able to add their favourite accounts. Again, how this will turn out and if it will be of any use at all remains to be seen. However, the development of Nitter is being handled by anonymous developer/developer Zedeus, whose GitHub you can publicly peek at.
Conclusion
Encrypted technologies can give us a lot, but they are far from being the only tool for increasing privacy on the Internet. Our data comes in many forms, and thanks to the devilish network effect, probably none of us can afford to live purely on encrypted communications. At least not yet. Timothy C. May, for example, begins his Cryptoanarchist Manifesto with the optimistic sentence "…Computer technology is on the verge of providing the ability for individuals and groups to communicate and interact with each other in a totally anonymous manner…".
So if you want to help fulfill Timothy C. May's vision, or if you're just a fan of security and privacy on the Internet, then you should nag people and increase the network effect of open and encrypted technologies. Whether we want to or not; it's the nework effect that will always be a crucial marker of why someone is/isn't motivated to use a technology.
As mentioned earlier, we all evaluate risk and privacy a little differently. However, if we are evaluating it, and we want to evaluate it sensibly, we should, first of all, know as much as possible about the tools and techniques that we are using. We all prefer something different, and there is no such thing as a one-size-fits-all tool for anything, including communication or social networking. However, if any part of the article made you think and install any of the apps mentioned, I consider it a success.




