The Wall Against Big Brother II. – Browser Extensions

In the last episode of The Wall Against Big Brother, we explained how browser fingerprinting, cookies, local/sessionStorage, and other tracking tricks that lurk on the Internet work. In this section, however, we'll focus on protecting our privacy. Specifically, with the help of browser extensions.
To disable or not to disable
JavaScript is a very crucial initiator of internet tracking. It's so crucial, that if we don't completely disable JavaScript on our browser, it's impossible to avoid tracking.
There are also separate browser extensions for disabling JavaScript, which we'll get to, but as we already know from the last article, JavaScript is not only responsible for tracking. It's responsible for a lot of things that make web pages usable in some way (for example, many online maps, game engines, or web servers can't function without JavaScript). Therefore, I personally prefer not to disable JavaScript on my browsers.
However, this article is not meant to encourage anyone on what to do or not to do. Whether we disable JavaScript is up to each of us, just be aware that if we do, we will create a lot of problems with the functionality of our websites. And by the way, I find turning it off to be counterproductive from a privacy point of view, as I consider such an action to be too suspicious for Big Brother.
NoScript
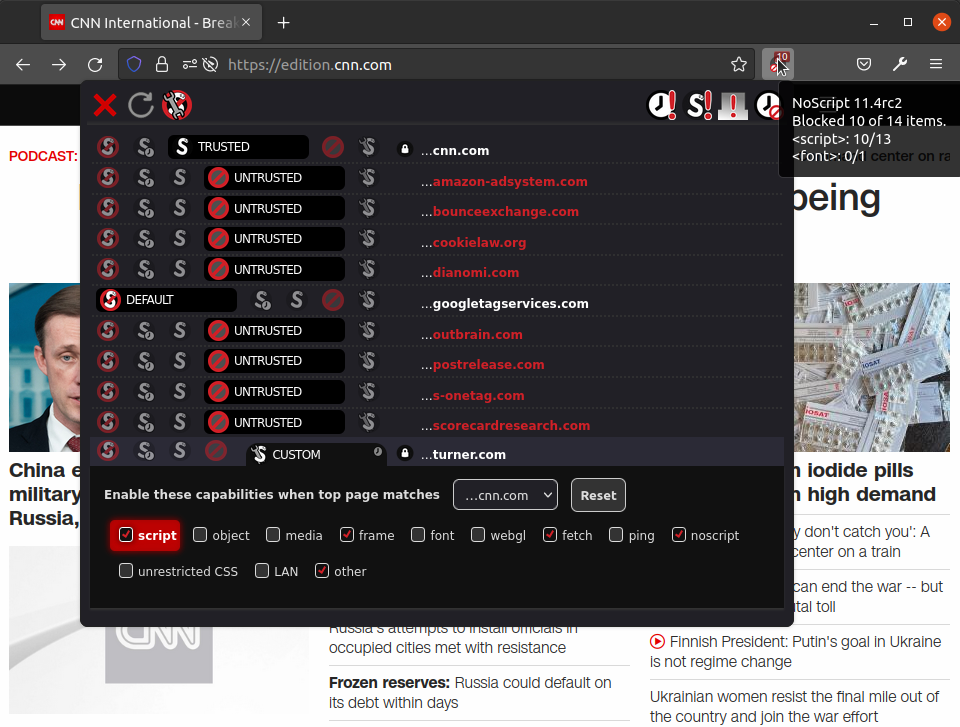
NoScript is an open-source extension that won the "PC World - World Class Award" and is included by default in Tor Browser. However, it is also available for Mozilla and Chrome. It allows you to run JavaScript, Flash, or other executable content only from trusted domains of your choice.
With its unique ClearClick technology, it protects your "trust boundaries" from cross-site scripting (XSS) attacks, cross-zone DNS rebinding/CSRF (router hacking) attacks, and clickjacking attempts (an attack where a user somehow takes an action – such as clicking a button or image – that he or she didn't expect).
If some of the terms are foreign to you, don't panic. Simply put; NoScript protects us from Big Brother's influence and makes your browser safer with it.
ScriptSafe
ScriptSafe is something like NoScript purely and only for Chrome. Literally. It's also open-source.
Some users claim that ScriptSafe's interface is a bit clearer and more intuitive compared to NoScript, but at the toll of customizability.
uBlock Origin
uBlock Origin is my favorite, which I prefer over NoScript, btw. It may look like a simple ad blocker, but it can do much more. It's a pretty advanced content blocker that also specializes in improving CPU and memory efficiency.
uBlock Origin blocks ads, trackers, coin miners, popups, etc. through the following list of filters that are set by default in the extension:
- EasyList (ads)
- EasyPrivacy (tracking)
- Peter Lowe’s Ad server list (ads and tracking)
- Online Malicious URL Blocklist
- uBlock Origin's own lists
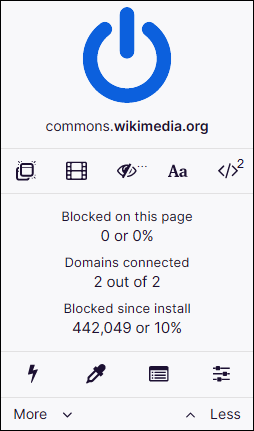
However, if you want to have more control over uBlock Origin, you can use its "advanced mode" to set up lots of other things. Just go to Settings and click on the "I am an advanced user" box. Thanks to this feature, you can even completely disable JavaScript on uBlock (locally for the site or globally for the entire browser). You can also create your own global and local rules for overriding individual entries from filter lists and many other advanced features.
uBlock origin in default mode supports only static filtering, while in advanced mode it also supports dynamic filtering. But what does it exactly mean?
Static filtering refers to filters that come directly from the specific filter lists we mentioned above (e.g. EasyList, EasyPrivacy, etc.), while dynamic filtering consists of filtering rules that are somewhat firewall-like in their nature.
Simply; dynamic filtering rules override static filtering rules, and this means that dynamic filtering can override all existing static filters with permission. So with dynamic filtering you can block with 100% certainty.
You can find more details about dynamic filtering as well as customizing uBlock Origin at this link.
uBlock Origin is fully open-source and is available for both Mozilla and Chrome.
Privacy Badger
Privacy Badger is a great option for anyone who doesn't want to disable JavaScript (for the sake of website usability), but still doesn't want to be tracked by Big Brother. We could say that this approach doesn't "prevent a fire from starting", but it does "prevent a fire from spreading".
As we have already mentioned, tracking is unavoidable without disabling JavaScript. PrivacyBadger, however, automatically blocks invisible trackers. So how does it do that?
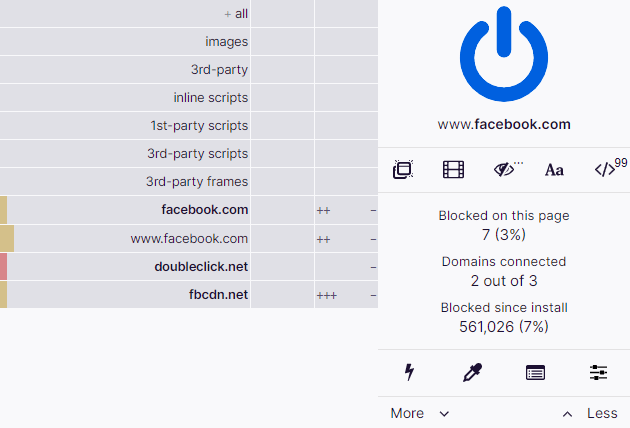
If you're viewing a web page, that web page is often made up of content from a variety of sources (for example, a news website might load an actual article from a news company, ads from an advertising company, and a comments section from another company that has been contracted to provide that service). Privacy Badger tracks all of these. If, while you are browsing the web, the same source appears to be tracking your browser on different websites, Privacy Badger will take action and tell your browser to no longer load content from that source. And when your browser stops loading content from a source, that source can no longer track you. And that's it.
On a more technical level, PrivacyBadger records third-party domains that load images, scripts, and advertisements into the websites you visit. Thus, it also searches for cookies, canvas fingerprinting, but also localStorage (which you already know a bit about from the last article). If Privacy Badger detects that one third-party host is tracking you on e.g. three different sites, it will automatically disallow content from that third-party. In doing so, Privacy Badger sends a Do Not Track signal to those "third-party companies".
In addition, Privacy Badger is regularly updated and learns thanks to the Badger learning project, which automatically discovers trackers present on thousands of websites from around the world. Thus, by default, Privacy Badger does not learn from your browsing, because it is precisely this "local learning" that can make websites better able to identify you after all, as they learn "locally from you".
HTTPS Everywhere
HTTPS Everywhere is an open-source extension for Chrome, Firefox, Opera and many other browsers. It was developed in collaboration with the Electronic Frontier Foundation and, just like NoScript, it can be found by default on Tor Browser.
What HTTPS Everywhere practically does is that it automatically switches websites from the insecure http protocol to the secure https protocol.
Yes, it's true that e.g. Mozilla Firefox web browser has an "Enable HTTPS-Only Mode" setting option in the "Privacy & Security" section, but unlike Mozilla, HTTPS Everywhere is a bit more customizable and allows you to turn https-only mode off for some specific sites of your choice.
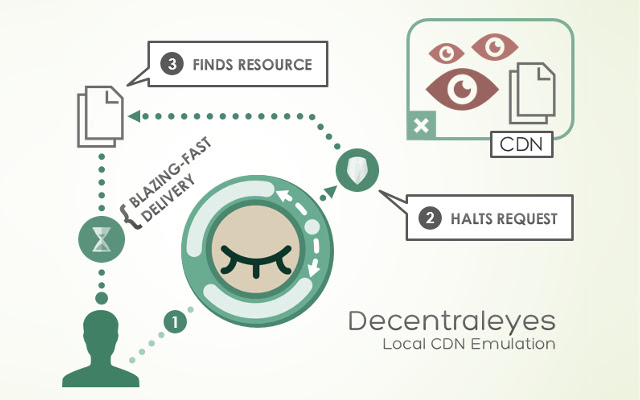
Decentraleyes
Decentraleyes is another great extension, which is dedicated to local emulation of content delivery network (CDN). But what does it mean in human language?
Well, JavaScript, our favourite programming language – just like any other programming language – needs some code libraries. These libraries should be loaded by our CDN (content delivery network). Since thousands and thousands of websites use somewhat common CDNs, it is very easy for CDNs to track users across websites. Not surprisingly, classic CDNs include, for example, Google Hosting Libraries.
However, if you care about your privacy, you probably don't want the libraries to be loaded via Google and other Big Brother shenanigans. Decentraleyes, for instance, automatically blocks Google Hosting Libraries and other CDNs and instead provides code libraries (such as jQuery or AngularJS) locally on the user's machine.
User Agent Switcher
Warning – at the time of writing, User Agent Switcher is not monitored by Mozilla!
Have you ever needed to quickly switch between user-agent strings? Are you developing a website that needs to work in both mobile and desktop browsers? Are you fed up with some archaic site blocking you because you're not using Netscape 4?
User Agent Switcher solves all of the above. With this extension you can quickly and easily switch between user-agent strings. You can also set specific URLs to spoof each time.
Many parts of browser fingerprinting can undoubtedly be prevented with the User Agent Switcher, but this extension also finds its use in security in addition to privacy. How is this possible? Well, for example, if you are a Windows user and someone has prepared a nice Windows .exe virus for you, this virus will not work on "Linux". And you don't have to switch from Windows to Linux for that. Just use this handy extension and spoof your operating system with it :)
Of course, nothing is flawless. Beware that some sites may have their own specific detection mechanisms to discover that your browser is not what it pretends to be. User Agent Swicher can affect browsing performance due to the need to intercept and modify data communicated to the server, among other things.
Multi-Account Containers
It's true that this article is mostly about classic browsers like Firefox and Chrome-based stuff (Chromium, Vanadium, Brave) and doesn't really address e.g. Mac's Safari. This is primarily because browsers like Safari have a slightly different cookie/tracking policy in the first place, and aren't as highly customizable via extensions as their non-Mac colleagues.
When choosing "the safe" browser, most people choose chrome-based browsers for some reason, and especially Brave, which is known as "the browser that emphasizes privacy because it blocks ads".
Paradoxically, I think it is possible to find better privacy on Firefox than on Brave. And it's mostly due to my favourite extension "Multi-Account Containers".
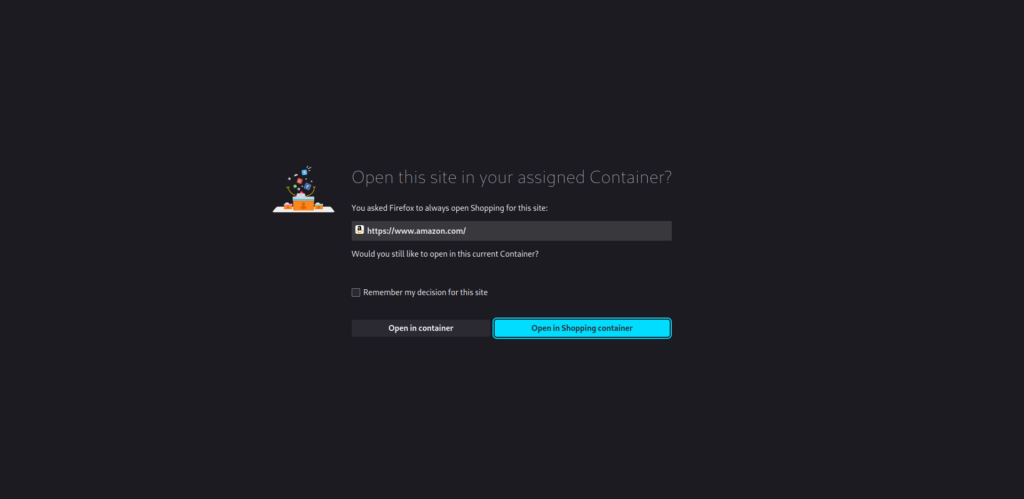
What Multi-Account Containers do, in short, is that they allow you to designate separate containers for each of your online lives (so you don't have to use a different computer or virtual machine just to open your work email).
There are Personal, Work, Banking and Shopping containers. You can open a particular web page in one specific container and once you visit it again, Firefox remembers that container and asks if you want to open that page in that container each time (see image below). If you check the "Remember my decision for this site" box, you're all set. You can bookmark the site and it will open in the container of your choice every time.
But how does it work under the hood?
Multi-Account Containers divide a website's storage into containers, with cookies in one container not being available to other containers. You can even integrate individual containers with Mozilla VPN to protect your browsing and location.
Fluff Busting Purity and Facebook Container
If you already have your browser divided into individual containers, you should definitely know that Mozilla has more detailed containerization available. And it's specifically for big-brother social networks.
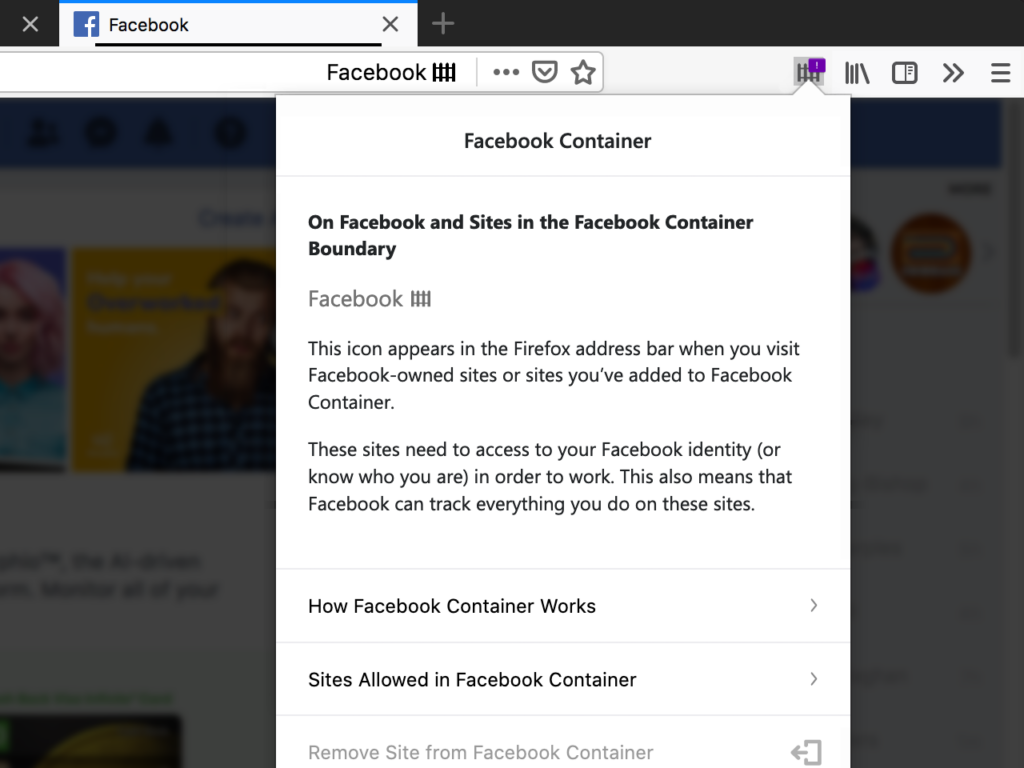
There's a Facebook Container extension that literally creates a container purely and only on your Facebook in the browser. This undoubtedly makes it harder for Facebook to track your visits to other websites using third-party cookies.
Installing this extension will close your Facebook tabs, delete Facebook cookies and it will also automatically log you out of Facebook. If you then visit Facebook, this time it will already open in a new specific container (similar to how it did with the Multi Account Containers extension). In that container, you can now log in and use Facebook normally.
If you click on a non-Facebook link in the container, or go to a non-Facebook web page, those pages are already loaded outside of the container.
The Facebook Container can also be used for Instagram, but using the web version of Instagram is pure masochism from my perspective.
However, the containerization of Big Brother cookies is not everything. If we visit a given social network, there's a huge amount of unnecessary noise lurking there, playing with our user's attention. But no worries, we can handle it.
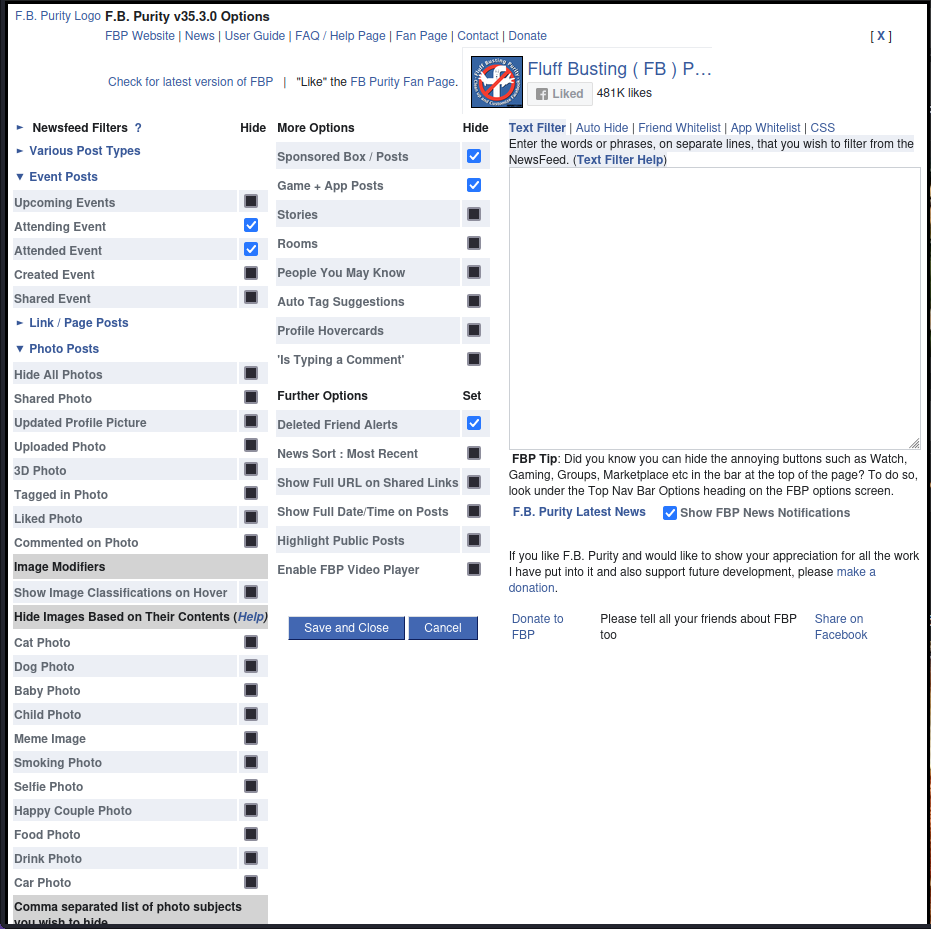
We have the Fluff Busting Purity extension, which specializes just in customizing Facebook's user interface.
It allows you to remove annoying and irrelevant posts from your newsfeed, such as ads and sponsored posts. I use F.B. Purity on my desktop as well and it always lets me know, for example, when someone unfriends me from Facebook. And I know his/her name and also the time of unfriending. Or I can also filter out all posts containing the word “coronavirus” :)
F.B. Purity has been around since 2009, its one of the top 150 highest user rated Firefox extensions (out of a total of over 11,000 extensions) has over 481,000 happy users and has also received glowing reviews from big media companies including The Washington Post, CNET and PCWorld.
Conclusion
We've gone through some web browser extensions together, but the market for extensions is really big. However, if you care about privacy and security, you need to be especially careful about whether the extension is from a well-verifiable source, what reviews it has, and how many people are actually using it. In fact, we can find a huge number of recommendations from YouTubers and bloggers for such and such extensions on the Internet, which ultimately turned out to be not very secure solutions. A good example is the Ghostery extension, which YouTube is full of and which pretends to be an advanced privacy-oriented content blocker, but it was already known in 2013 that this extension sells data to advertising companies.
Of course, web browser extensions aren't everything. Privacy pitfalls also lurk in specific search engines and browsers. And of course, as it happens, this problem also affects search engines and browsers that proudly pretend to be "privacy-oriented". But more on that next time.




