What is a Warrant Canary and How to Use it for Your Website

It happens quite often nowadays that government parasites issue secret subpoenas to certain online service providers.
These businesses are then legally forbidden from disclosing this fact, putting users' data and privacy at risk.
However, service providers found the way around it without breaking any laws by using a so-called Warrant Canary.
What is a Warrant Canary?
A Warrant Canary is a regularly updated statement which an online service provider uses to let their users know that the provider hasn't been served with a secret government subpoena.
It's usually a text file named canary.txt that contains a cryptographically signed message and a signature that the above statement is true.
There are cases when users should assume the service has received such subpoena:
- The signature was tampered with
- The statement wasn't updated in a while
- Warrant Canary disappears with no explanation
In that case, users should stop using the service immediately because their privacy may be in danger.
Read EFF's Warrant Canary FAQ to learn more.
How to Check its Validity?
Let's see how to check a warrant canary for our site freedomnode.com. You can, of course, apply this method for any other site that has one.
Before we start, make sure you have a GPG tool that supports OpenGPG standards first. I use GPG Suite on Mac OS X because it adds encryption to the native Mail app.
On other systems, you may use one of many open source frontends for GPG command line such as GnuPG Shell.
Once you install a GPG tool create a cryptographic key pair which comprises of a public and private key.
Fill out the form and choose a strong password.
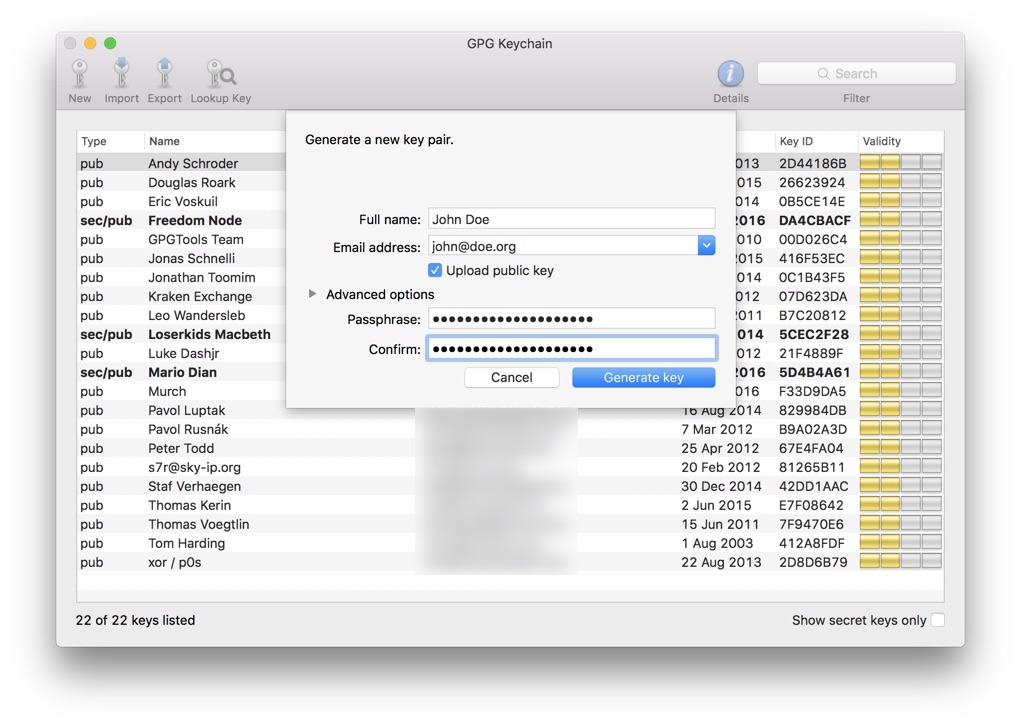
Also, make sure "Upload public key" is selected. It will upload your public key to a public key server such as https://pgp.mit.edu.
Get a Site's Public Key
Now, let's get Freedom Node's public key so we can verify the cryptographic signature. Skip this step if you already have it.
Go to MIT PGP Key Server and search for "freedomnode". Make sure "Show PGP fingerprints for keys" is selected.
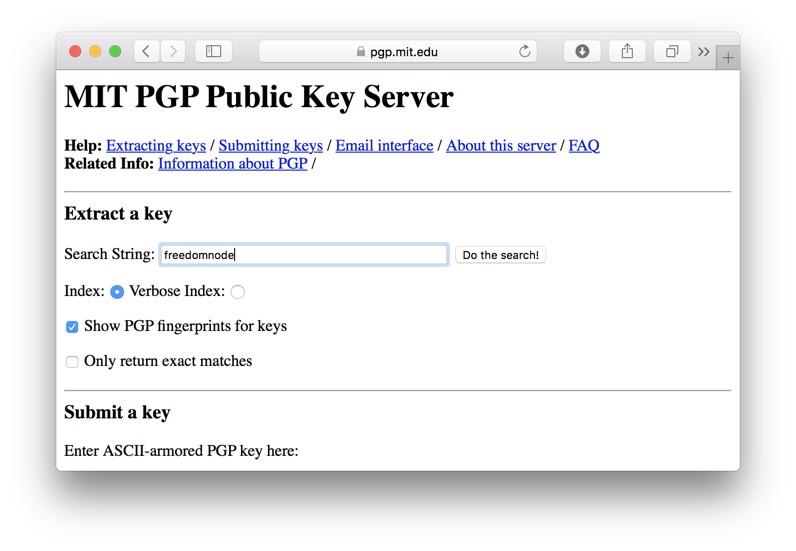
Take note of the key fingerprint.
Open our Warrant Canary file and look for the fingerprint.
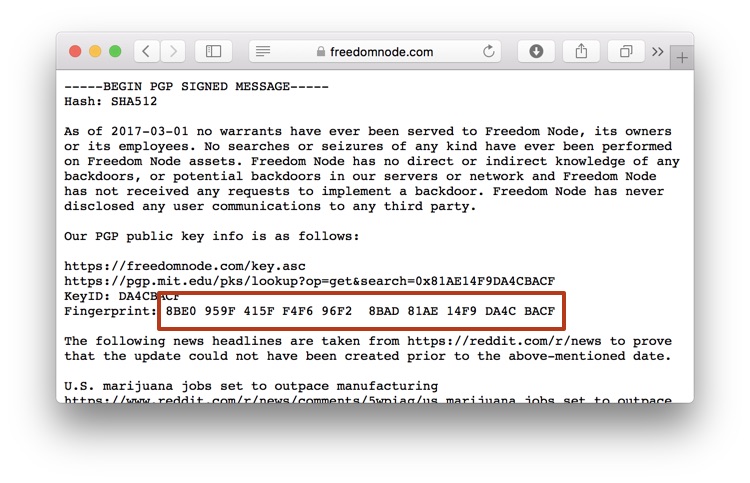
They have to match!!!
If they don't, stop using our services immediately. We've been "gagged", and the file was very likely modified by the government.
Otherwise, check the fingerprint on our keybase profile as well.
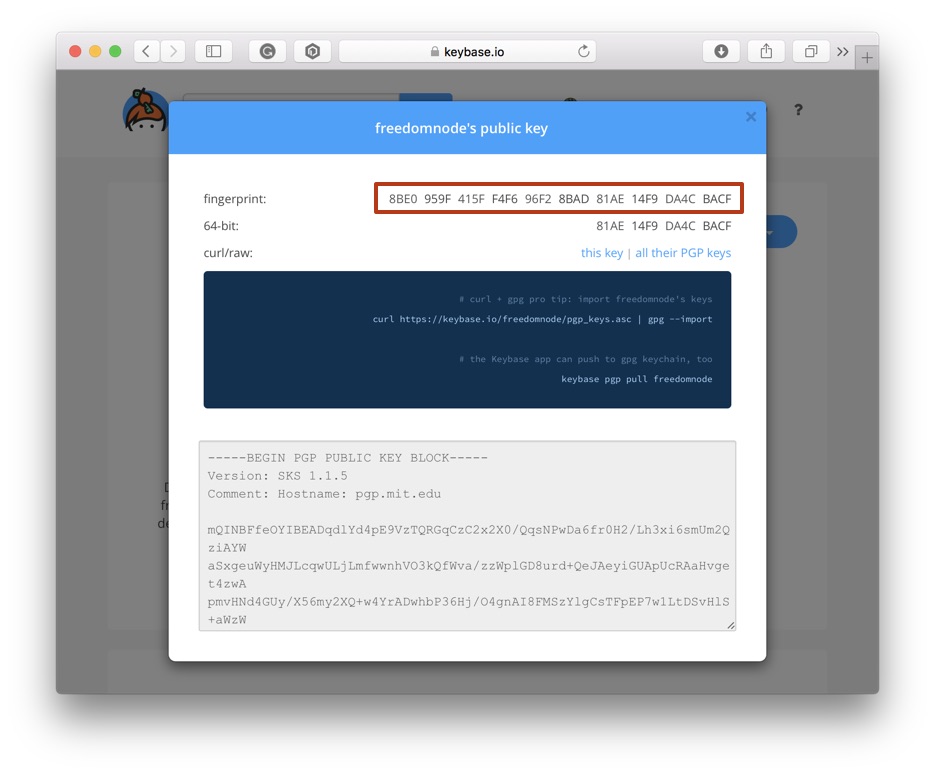
Everything looks okay.
Verify a canary.txt File
Go back to canary.txt and take note of the date at the top of the file.
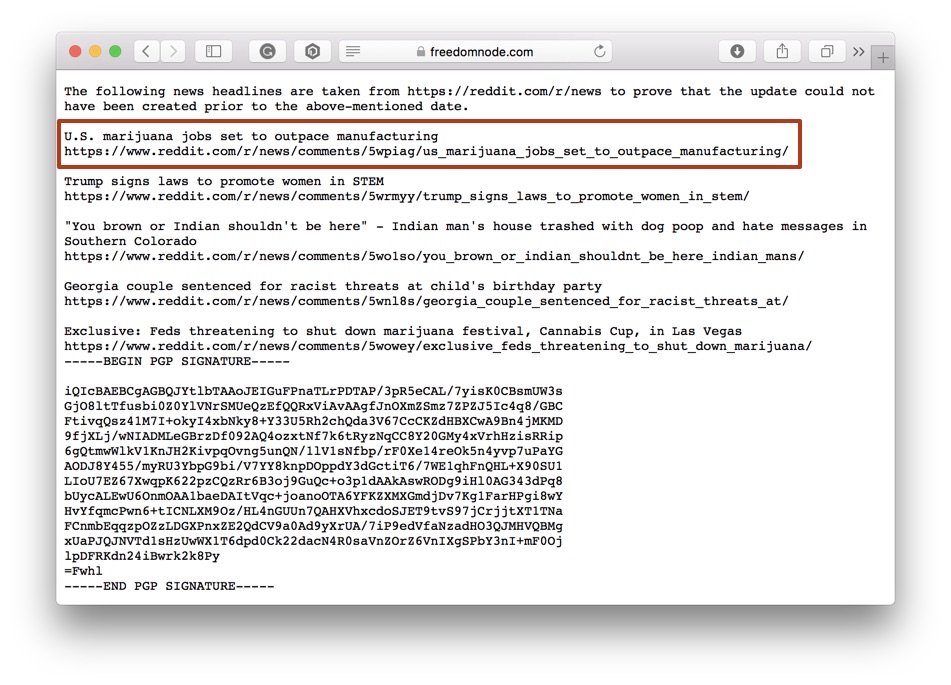
It shouldn't be older than a month or so.
Scroll a bit further where you'll find news headlines and links taken from /r/news. Open every one of them.
Make sure they are older than the above date! It proves the canary.txt update could not happen before articles were published.
If you can't open provided links, try to find them on Google using their headlines.
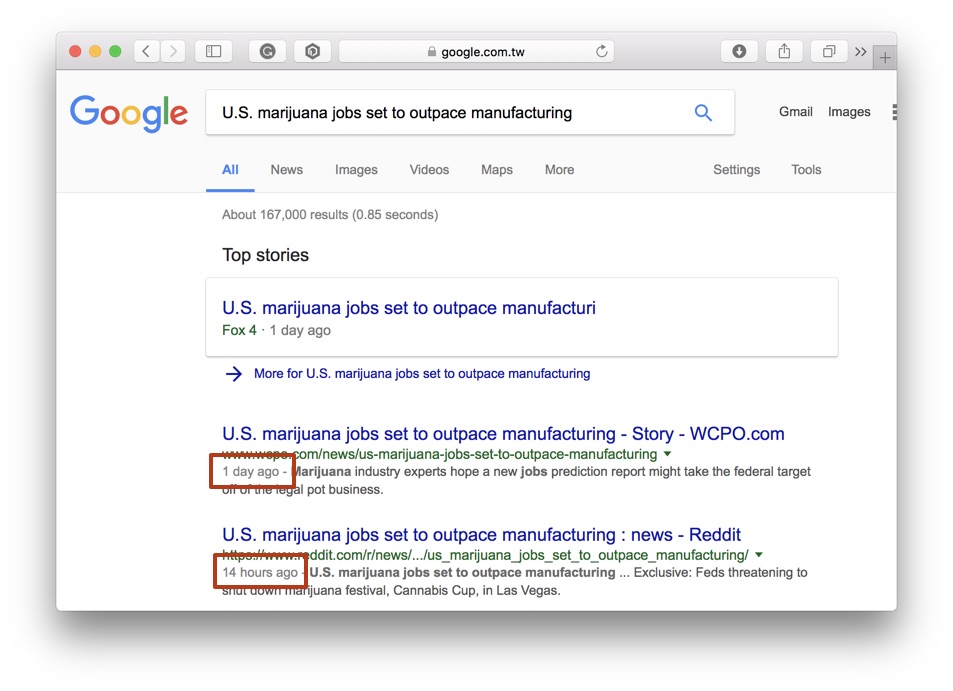
So far so good. Now onto the more interesting part.
You can see that the text of canary.txt is encapsulated in
-----BEGIN PGP SIGNED MESSAGE-----and
-----END PGP SIGNATURE-----It tells us where the signed message and the signature signed (hopefully) by the owner of the website begins.
Save it to a text file - let's call it signature.txt.
Note: some websites include a description of what a Warrant Canary is and how to verify the signature at the top of the file.
Locate the newly created file, right click it and choose Services -> OpenPGP: Verify Signature of File.
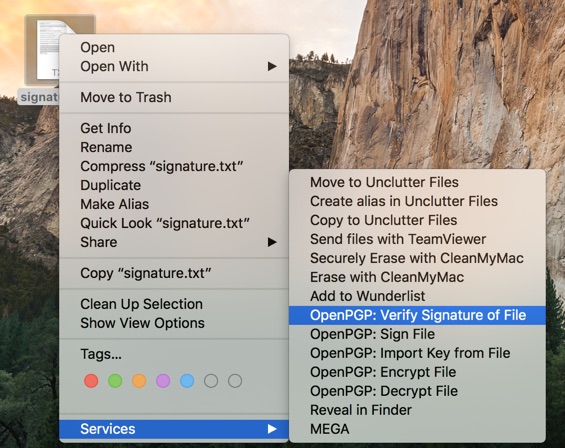
With the "magic" of asymmetric cryptography, OpenPGP will now use the site's public key that we've imported to verify the signature.
Once verified, we can be sure that the warrant canary is indeed signed by who it claims to be.
However, this method isn't 100% bulletproof. The government may forcefully coerce site owners to update their Canary effectively faking the statement. Keep that in mind!
How to Create a Warrant Canary for my Site?
If you run an online service, you should prepare for future gag orders too. You never know when you and your users fall victim of the government violence.
Looking at the Freedom Node's Canary, it's obvious what kind of information a good Warrant Canary should contain.
But let's recap it again:
- Date of Canary update
- Statement that the site hasn't received any "gag order" to the given date
- Links to the public key and its fingerprint
- Recent news headlines and links used from a reputable source (/r/news, Reuters, etc.)
You can use the following template for your Warrant Canary:
As of [File update date] no warrants have ever been served to [Your site name], its owners or its employees. No searches or seizures of any kind have ever been performed on [Your site name] assets. [Your site name] has no direct or indirect knowledge of any backdoors, or potential backdoors in our servers or network and [Your site name] has not received any requests to implement a backdoor. [Your site name] has never disclosed any user communications to any third party.
Our PGP public key info is as follows: [Link to your public key(s)]
KeyID: [Public key ID]
Fingerprint: [Public key fingerprint]
The following news headlines are taken from [News source] to prove that the update could not have been created prior to the above-mentioned date.
[News headline] [News URL]
[News headline] [News URL]
[News headline] [News URL]
[News headline] [News URL]
[News headline] [News URL]
When you're happy with your statement, select it, right click and choose Services -> OpenGPG: Sign Selection to New Window.
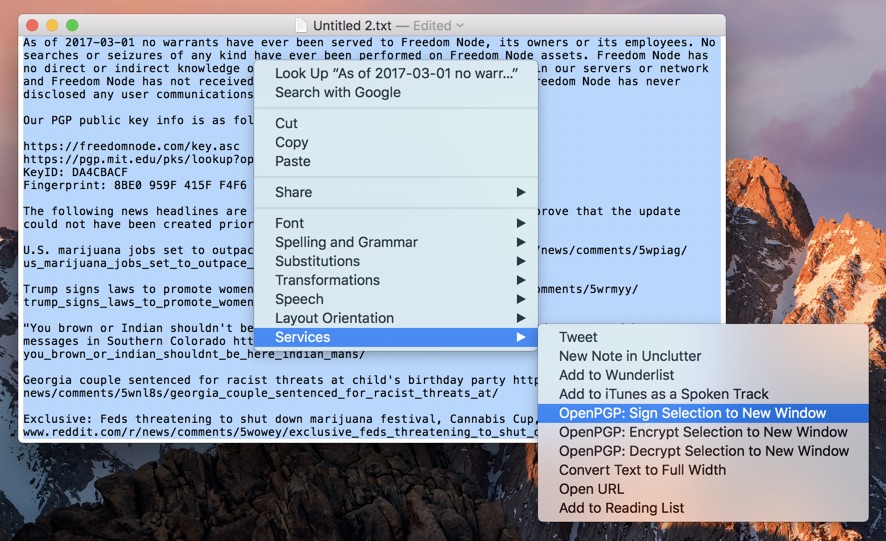
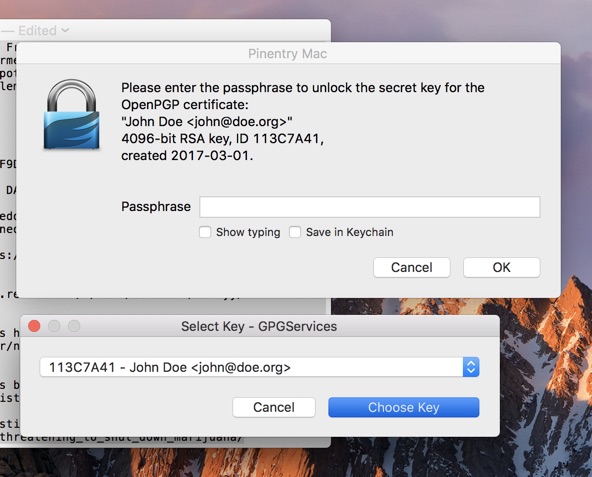
If you have more than one private key, choose the one of which the public key is shared with your audience.
Sign the message with your password.
It will create a signed message along with a signature in a new window.
Copy & paste it to a new text file and save it as canary.txt.
Verify it using your public key (just to make sure) and upload it to the root of your website, so it's accessible from https://<your site>.com/canary.txt
Let your users know about its existence and don't forget to update it regularly!
If you have any issues implementing your Warrant Canary let me know in the comments section below.




