How to Protect your Privacy when Splitting and Claiming Monero Shitforks

Ever since Bcash split from Bitcoin in August 2017, the fork craziness took place and there are currently at least 10 Bitcoin shitforks that I know of.
Monero suffered the same fate.
Monero shitforks, however, are considered an outright attack on its privacy and namely ring signatures (1 out of 3 main privacy features of the coin) because of the key reuse.
Fortunately, these attacks can be manually mitigated when shitfork developers aren't willing to implement a shared ring database that does all the work for you.
While it's best to completely ignore shitforks, the temptation to get "free" money is stronger. In that case, I urge everyone that cares about Monero's health yet is greedy to pay attention to the following tutorial.
When making a Monero transaction and creating a ring signature, decoy inputs are chosen from the TXO (transaction output) set along with your real input.
Since you'll be sharing the same private key in a shitfork wallet, the same key images may be created.
The issue is that they will contain a different set of decoys but the same real input.
Let's consider the following example:
Monero: key_image_X decoy_A decoy_B decoy_C decoy_D real_input_I
Monero Shitfork: key_image_X decoy_E decoy_F decoy_G decoy_B real_input_I
Whoever is able to analyze the transaction on both chains will be able to tell decoys from the real input since only the latter repeats within the same key image.
This lowers yours and everyone else's anonymity set.

To mitigate the above, it's important to set the same ring in your Monero wallet right after you make a transaction (e.g. deposit to an exchange market) on a shitfork chain.
Let's say you want to claim MoneroV.
MoneroV devs said they support the shared ring database and the below procedure is not necessary, but I haven't audited their code myself thus I want to make sure my privacy is protected.
Open MoneroV's monerov-wallet-cli and type:
show_transfersYou'll get the list of your Monero transactions pre-fork as well as MoneroV txs.
It looks something like this (real txs fake amounts):
1526760 out 2018-03-10 12.154690000000 d25baf7520dbce1d6f01baa987699df135d09b6fb33f595c1a97364acd799657 eac55afbfa714ebe 0.000818508520 494fBZtnTPFcTzJopNPpUtbEm7SayvAdohkyYAsCzZ6q3tLMaKjx7PWGvPAQjK9grbG6CUrd9kVsi6kWvF9K17UrPTzQab3: 12.154690000000 0 -
1578462 out 2018-05-27 4.335127600000 cb0f6388e858e0eebb2debf2319e13af25ff47d34afd4d6642b529e394e33c51 6e70feab552f7461 0.00072153885 494fBZtnTPFcTzJopNPpUtbEm7SayvAdohkyYAsCzZ6q3tLMaKjx7PWGvPAQjK9grbG6CUrd9kVsi6kWvF9K17UrPTzQab3: 4.335127600000 0 -The first transaction happened pre-fork, the second transaction happened on the MoneroV chain and is what we're interested in.
Copy the first hash (a transaction ID) on the shitfork chain and open the following on your browser via VPN (wait until it's fully loaded, it may take some time depending on the number of mixins of the transaction):
https://monerovexplorer.com/tx/<transaction id>/1
I used Chrome, but it should work on any browser that has a developer console.
Press ctrl + shift + I if on Windows or Linux and cmd + option + I on Mac to open the browser's console.
Switch to the Console tab and paste and execute the following javascript code:
javascript: (function(e, s) {
e.src = s;
e.onload = function() {
var json = $.parseJSON($('#decoded-inputs code').text());
json.vin.forEach(function(item){
console.log("set_ring " + item.key.k_image + " relative " + item.key.key_offsets.join(' '))
})
};
document.head.appendChild(e);
})(document.createElement('script'), '//code.jquery.com/jquery-latest.min.js')It injects jQuery into the website (it may take a few seconds) and retrieves key_image and key_offsets of the transaction.
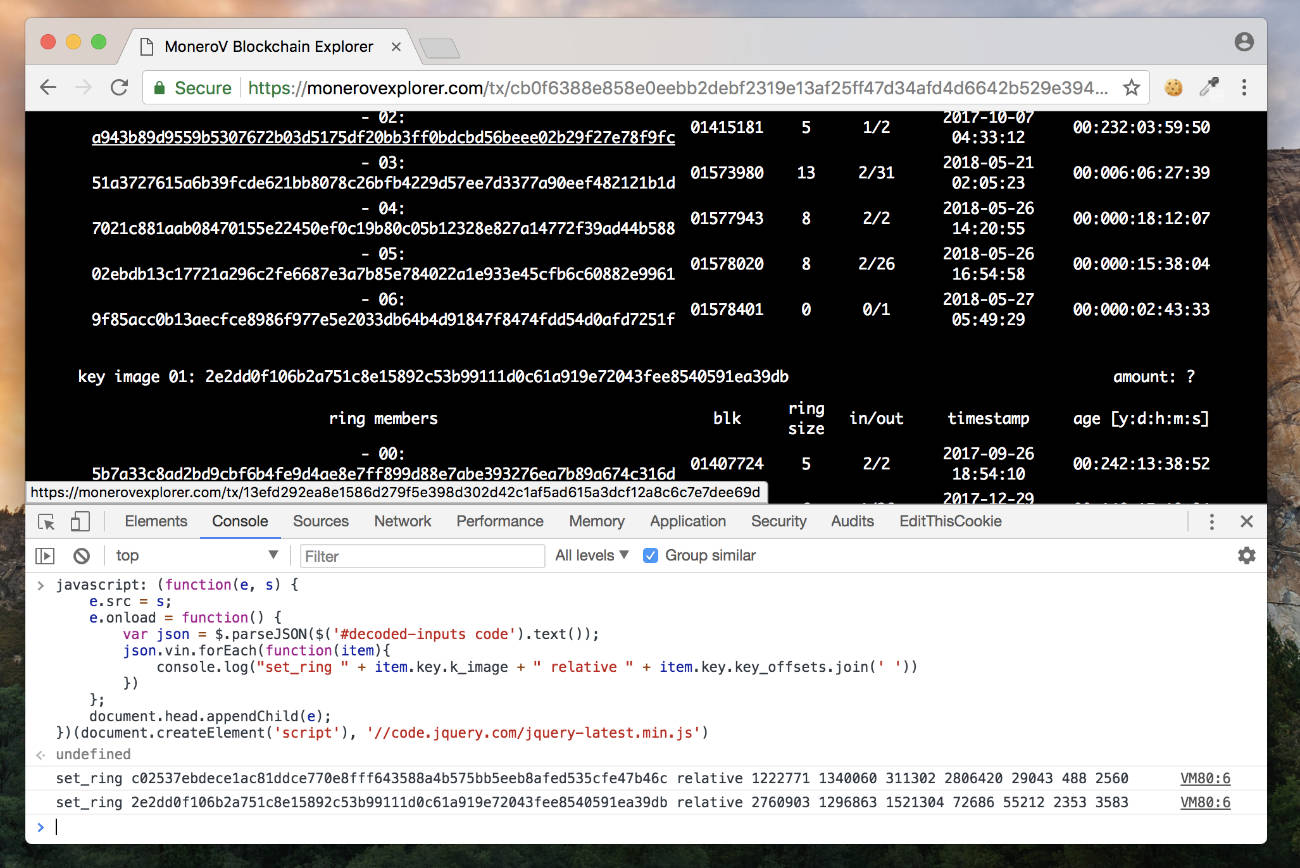
It also formats it into a monero-wallet-cli syntax:
set_ring c02537ebdece1ac81ddce770e8fff643588a4b575bb5eeb8afed535cfe47b46c relative 1222771 1340060 311302 2806420 29043 488 2560
set_ring 2e2dd0f106b2a751c8e15892c53b99111d0c61a919e72043fee8540591ea39db relative 2760903 1296863 1521304 72686 55212 2353 3583Please note, that instead of using a centralized block explorer, you can also get the above information via print_tx command within your full node.
Open Monero's monero-wallet-cli and execute each of the above set_ring commands.
From this point, every time you make a Monero transaction with the above key images, the ring members will always be the same as with MoneroV and nobody can tell decoys from the real input.
While Monero's anonymity set will still get a bit smaller with each shitfork transaction you make, the impact is much less severe than if you didn't do the above procedure.
If you want to help grow the anonymity set, please join the 13 Mixin Day initiative.
Don't worry if you missed the date, you can join at any time and also feel free to change the number of mixins to anything other than 13 (preferrably higher).